Update README.md
This commit is contained in:
committed by
 GitHub
GitHub
parent
ba9f3f0992
commit
aa1d02b021
@ -7,7 +7,7 @@ psudohash is a password list generator for orchestrating brute force attacks. It
|
||||
|
||||
### Pentesting Corporate Environments
|
||||
System administrators and employees tend to use the Company's name (or a subset of the name) as password for Wi-Fi access points, network devices and application or even domain accounts. With the company's name as input and the most basic options, psudohash will produce a wordlist with all possible character substitutions, char-case variations and more. Take a look at the following example:
|
||||

|
||||

|
||||
|
||||
The script includes a basic character substitution schema. You can add/modify character substitution patterns by editing the source and following the data structure logic presented below (default):
|
||||
```
|
||||
@ -25,7 +25,7 @@ transformations = [
|
||||
### Individuals
|
||||
When it comes to people, i think we all have (more or less) set passwords using a mutation of one or more words that mean something to us e.g., our name or wife/kid/pet/band names, sticking the year we were born at the end or maybe a super secure padding like "!@#". Well, guess what?
|
||||
|
||||

|
||||
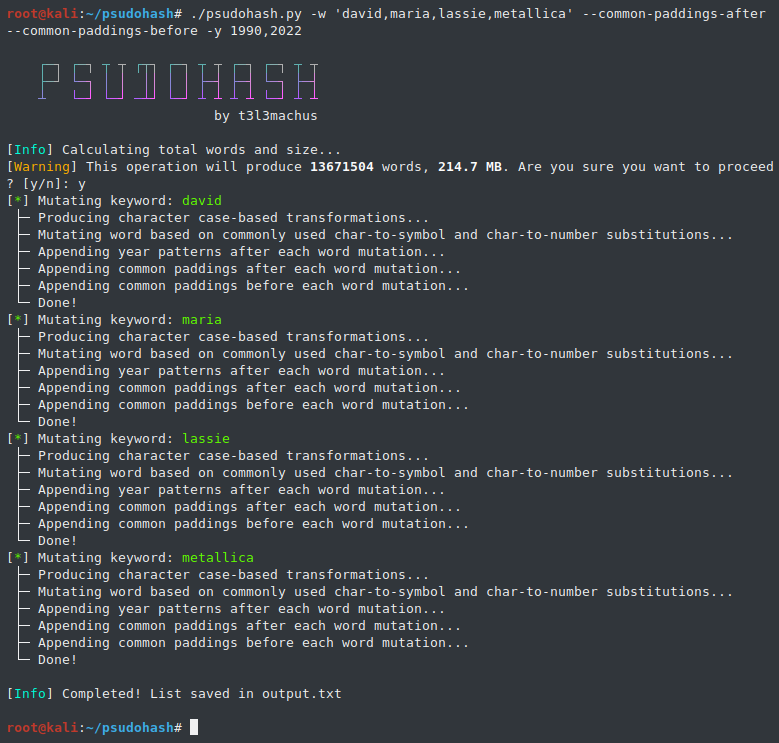
|
||||
|
||||
## Installation
|
||||
No special requirements. Just clone the repo and make the script executable:
|
||||
|
||||
Reference in New Issue
Block a user